Future of Networking – ZTNA (Zero Trust Network Access)
During the cold war, the Russian proverb “Doveryai, no proveryai” was very famous. US President Ronald Regan made its English version popular, “Trust, but Verify”, which became his signature phrase. Interestingly this principle of trust has come to prominence in the Cyber War as well. Its Avatar in Cyberspace is known as Zero Trust.
Why is zero-trust emerging as a new cybersecurity paradigm?
To answer this, let us understand evolution. We journey through the dot com boom, to be able to bring our own devices, to applications moving to the cloud, to now a world of computing turned upside down by the Pandemic.
There was a defined boundary to the network, and enterprises deployed security devices at this perceived perimeter for inspecting traffic & defining access policies.
The principle was simple- everything inside the perimeter is trusted and untrusted outside it.
This worked for a long time as enterprises deployed applications in data centers and gave access to these applications and data from branch locations through dedicated MPLS links. There were very few mobile users who needed access to corporate resources hosted in DC and managed through company-provided laptops & remote access VPN.
This approach was more focused on North-South traffic, i.e., from untrusted to trusted networks & rules were configured accordingly to inspect, allow, or deny traffic. The east-west traffic is a large chunk of the overall corporate data that flowed between the branches and the systems within a branch network, which was never inspected due to implicit trust. In this implicit trust model, enterprises configured security policies as if Insider threat does not exist.
The biggest business challenges traditional IT systems posed are that these IT systems are designed to work in the binary format “all or nothing” capabilities that made companies view security as overhead, productivity & revenue roadblock. Second, it relies on static policies to decide what is good or bad behavior at a single point in time; however, risk and trust are dynamic & ever-changing.
Imagine a scenario where your senior sales representative prepared slides for a presentation for your prospect’s key decision-makers. You try to copy the deck to a USB drive, but the configured rule denies it per your corporate security policy.
OR
Imagine another situation you have given access to roaming users. The account gets compromised & you get access requests from an unauthorized device to unusual access requests to the sensitive application. You do not have real-time posture validation, real-time geo-location data & a lack of analytics to detect behavioral anomalies or risky activities.
It does not mean that Zero Trust evolved to what it is today directly. Since 2010 the ZT approach took a fast-forward approach to reach the maturity of CARTA defined by Gartner.
We can build Zero Trust with existing technologies like legacy VPNs, Privilege Access Management (PAM) solutions, Firewalls & DMZ’s, placing applications behind a WAF, Using CDN’s to arrest DDoS, Provisioning VDI, MFA, etc. We did help many organizations in achieving some of the zero-trust principles based on the traditional security models.
Below are a few quick references, where we helped a few organizations using the principles of Zero Trust:
Zero trust-based identity & context-based access were the primary design goals of security architecture we designed for a private bank with 10k plus users almost a decade back. Network Admission Control (NAC) solution implemented with dynamic VLAN assignment & a captive portal for guest VLAN management. NAC solution ensured that only authorized device that falls in line with company security policy gets network access. The number of systems redirected to the remediation server for lack of posture was staggering & that feedback helped improve & automate the patch management process. SOC operations provided much-required validation regarding compliance and a single pane of glass visibility of the security landscape.
We implemented IDM & SSO for another bank that made application access provisioning simpler and dramatically reduced access-related operational & security incidents in the environment.
India’s largest print media company embarked software-defined network (SDN) journey with us. We completely transformed network access and WAN edge with the Cisco SDN solution. There was a significant improvement in end-user application access experience and enhanced security & visibility.
All this was fine till BYOD & Digital Transformation revolutionized the application landscape.
What is Zero Trust?
Today, the rise in cloud connection, the mobile and remote workforce has put users and devices’ visibility outside the traditional perimeter of the enterprise.
The perimeter has expanded beyond company walls, making it more difficult for security and IT teams to verify user and device identities before granting both access to enterprise applications and data.
A zero-trust model replaces perimeter-centric security architecture. It ensures that security and access decisions are dynamically enforced based on identity, device, and user context. A Zero Trust security framework also dictates that only authenticated and authorized users and devices can access applications and data.
Zero trust treats every access attempt as if it originates from an untrusted network.
The new perimeter is around the app, users, and their devices. Zero-trust is not only building the wall, but security teams also focus on what is inside the wall. Making destinations harder to attack, more resilient, and more resistant to attack by reducing the attack surface.
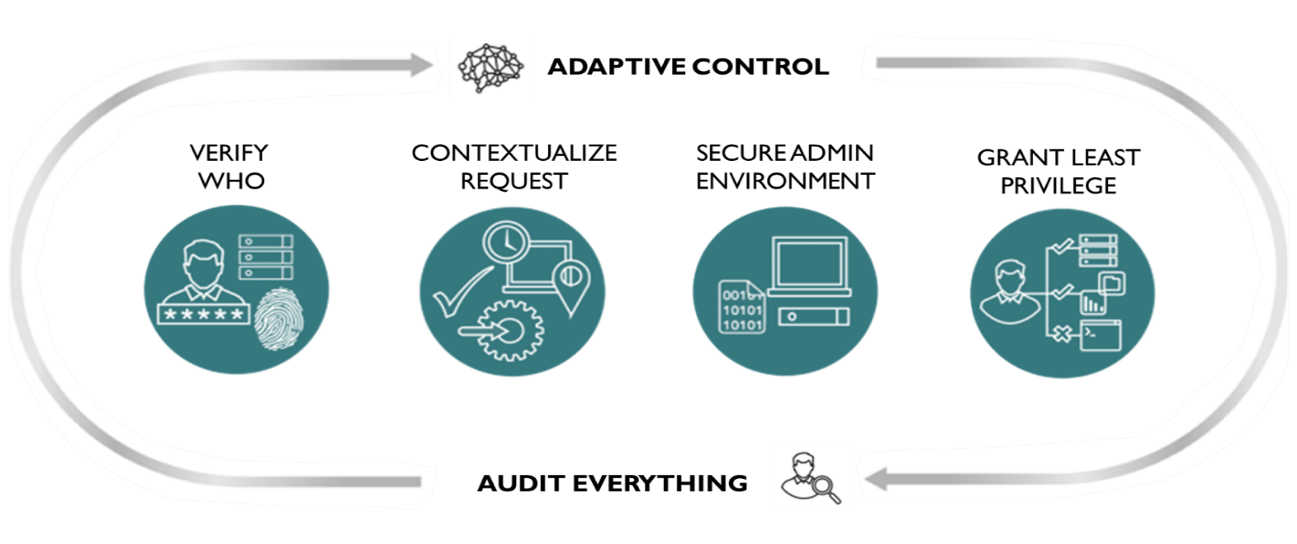
Zero Trust across the digital estate
Zero Trust is a philosophy rather than a tool that needs multiple technologies to put together a ZT approach. The diagram below shows how the major components of the Zero Trust model work together to deliver end-to-end coverage.
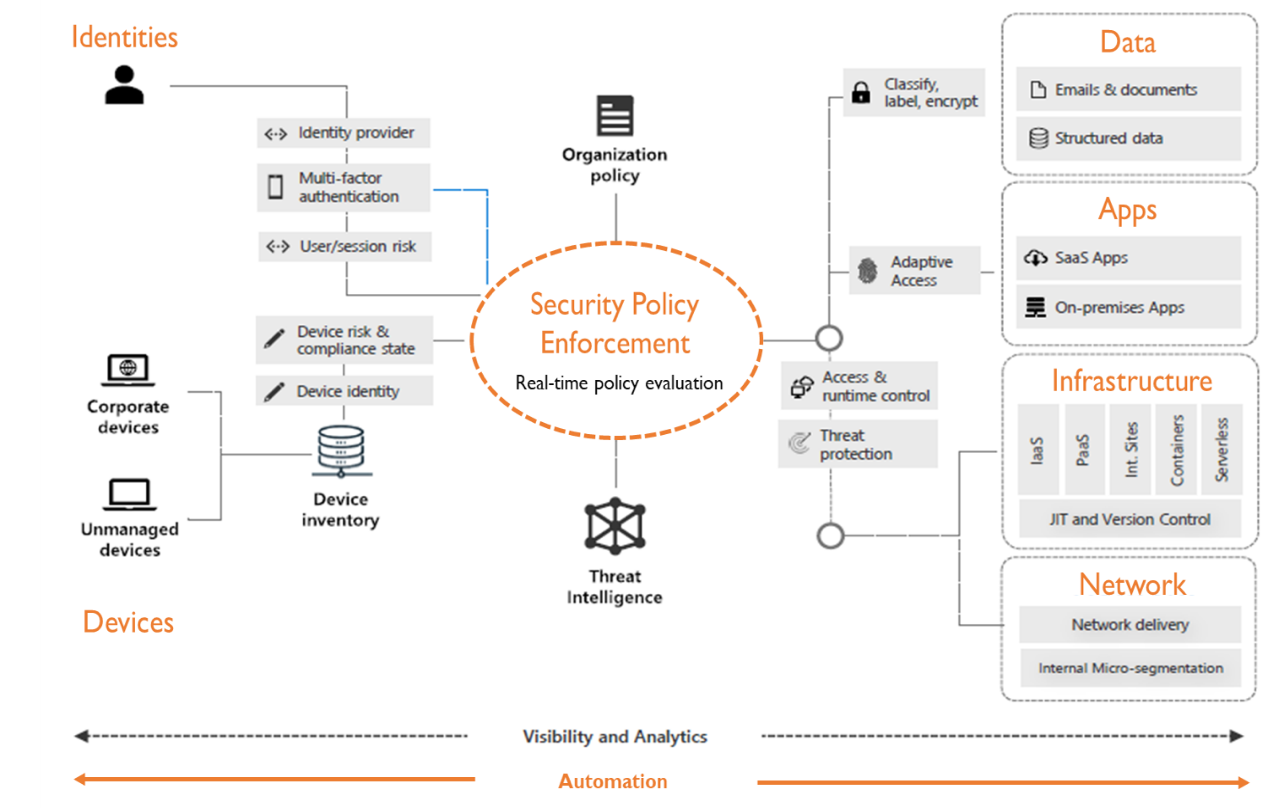
Zero Trust Architecture – Guiding Principles
Some of the guiding principles of the Zero Trust Architecture that an enterprise needs to follow are:
- Never trust, always verify: Do not inherently trust anything on or off your network. If you accept that you cannot control every IP address and every device, the result is that you can no longer assume trust within the network perimeter.
- Grant access based solely on the identity and device of the user accessing the application, regardless of a user’s network location—be it an office, a home network, or a coffee shop. You need to know that the user requesting access to a resource is who they say they are, and you need to verify that they can access that resource.
- Access controls are dynamic and must be continuously verified. In a zero-trust environment, consistent authentication and authorization checks are essential for maintaining security.
- Visibility and Analytics: To enforce Zero Trust principles, empower your security and incident response teams with the visibility of everything going on in your network – and the analytics to make sense of it all.
- Automation and Orchestration: Automation helps keep all your Zero Trust security systems up and running and your Zero Trust policies enforced. Humans are not capable of keeping up with the volume of monitoring events necessary to implement Zero Trust.
Zero Trust relies on a lot of security assumptions, as mentioned above. Traditional technology does not deliver on those assumptions; for example, Attackers can exploit VPN tunnels as it creates a hole in the network. Once the bad guys have network access, lateral movement becomes possible. Similarly, hosting non-public bits of an application in the DMZ exposes them to the internet & makes them discoverable.
The new reality is that more applications get hosted outside the data center, sensitive data in several cloud services, and users connect from everywhere.
The crucial question is, what technologies power the Zero Trust model? That is where the architecture for the cloud and mobile world called Secure Access Service Edge (SASE) comes into the picture. SASE is a confluence unified architecture of Zero Trust Network Access (ZTNA), also known as a software-defined perimeter (SDP); security (such as SWG, CASB, FW, and ZTNA) as a service delivered on the cloud edge.
If your organization is planning a Zero Trust journey, the first step could be eliminating legacy VPN’s by adopting ZTNA. The capabilities of ZTNA technologies are as follows:
- Micro-segmentation, not network segmentation.
- Application access without network access
- Mask applications from the internet with outbound connections
- Integrations with SAML for identity-based access
- The internet must become the enterprise’s new transport network.
- Integrations with technologies for traffic inspection for outbound traffic, monitoring for botnet calls, data loss prevention, and visibility into anomalous activities. It ensures an overarching security view across privately and externally managed apps.
At this point, you must be wondering if no VPN, no passwords, how a private application is accessed?
How it works:
- User authentication with IDP (first time only)
- Authorized user attempts to access an app; This creates a Client Connector tunnel.
- The SDP solution Service Edge enforces policy and sends a dispatch to connectors.
- The App Connector closest to the app sends outbound connections through a tunnel to SDP Service Edge
- The SDP Service Edge stitches together the connection between app and user.
We can use Gartner’s Continuous Adaptive Risk & Trust Assessment (CARTA) strategy to evolve Zero Trust security from rigid & reactive to flexible & proactive.
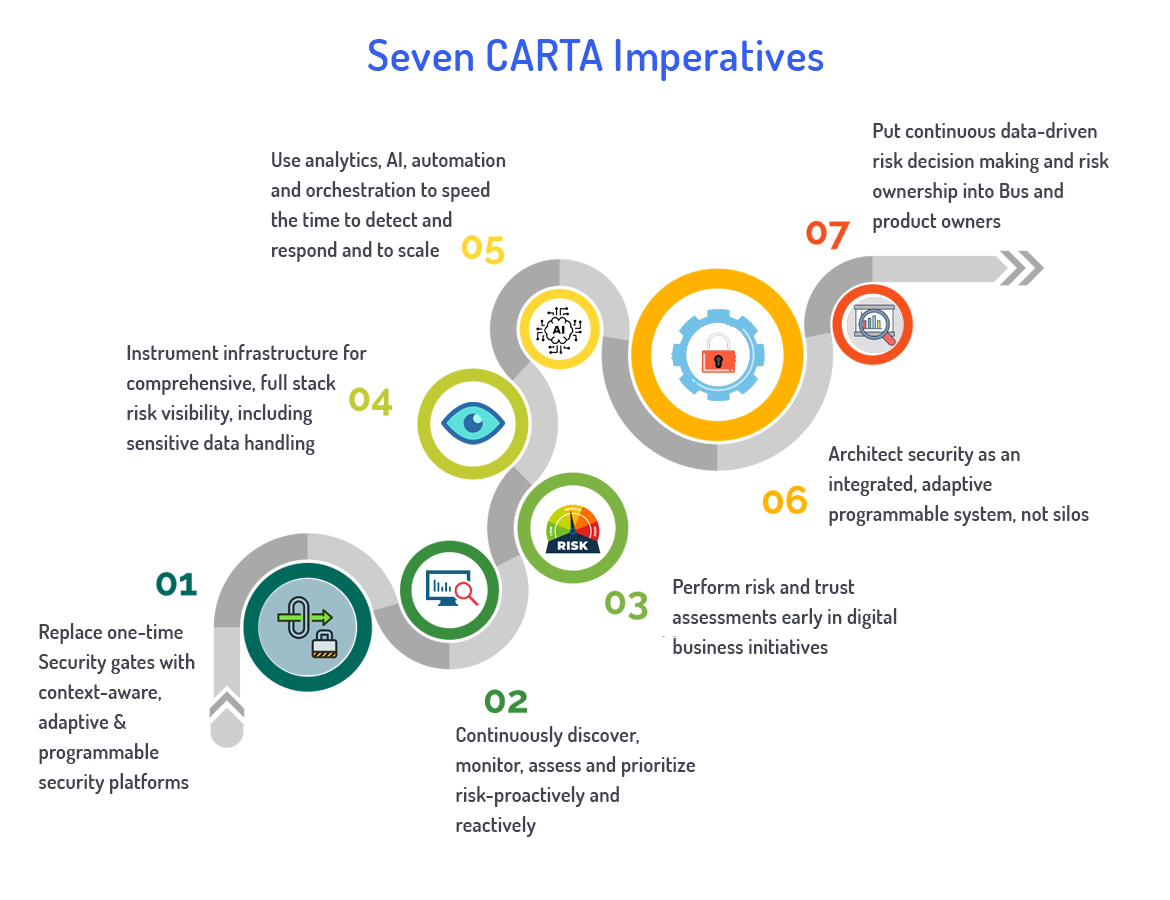
SASE capabilities help roll out CARTA features technically. We can use security solutions like SWG, CASB, FWaaS, Sensitive-data and malware inspection capabilities, Remote browser isolation, DNS protection, API-based access to SaaS for data context etc. We can integrate these from one or more vendors.
Use Cases of Zero Trust
- Work from Home – VPN less (anti-DDoS, Global Load Balancer, Firewall appliance) fast, secure private application access.
- Zero Trust On-Premises – Enable least-privilege user access to private apps without network segmentation.
- Secure multi-cloud access – enables migration to the public cloud by standardizing on a single security service that works across all cloud platforms.
- Secure Partner Access – Ensure contractors on your payroll get access to the right apps, not the network.
- Accelerated M&A integration – Mergers and acquisitions (M&A) typically require converging multiple networks and dealing with overlapping IP addresses because of network address translation (NAT). So ZTNA reduces complexity & accelerates IT Integration projects.
Benefits of Zero Trust
- Users are NEVER placed on the network.
- Internal apps are entirely invisible.
- Lateral movement gets eliminated.
- The internet gets used as a secure means of connectivity.
- Good user experience with Security & Simplification
- Browser access service eliminates the need for a client on devices.
- Proxy-based architecture for a full inspection of encrypted traffic at scale
- Brings security and policy close to the user to eradicate unnecessary backhaul.
- Zero attack surface that does not expose your source networks and identities to the internet, preventing targeted attacks.
- Remote access solutions, offer poor visibility into partner activity limited to IP address and port data. Zero Trust provides comprehensive visibility into all partner activity down to the user, device, and named app level.
Based on all these technological advancements around Zero Trust, the road to transformation is clear.
We live in a world of rapid adoption of cloud-hosted applications & mobility, creating cybersecurity gaps, but there lies a sea of opportunities businesses cannot afford to lose. To accommodate these disruptions in the digital landscape, we must incorporate dynamic risk evaluation based on a default-deny threat posture into security. Companies need to build security that makes sense in the cloud. That is where Gartner defined framework CARTA & solutions around SASE & ZTNA that makes secure digital transformation possible.
Related Topics:
Cloud Native and App Modernization Security concerns – Exploring Container Security


