Secure Access Service Edge (SASE) – All you Need to Know!
We have talked about moving away from security by traditionally securing perimeters-based approach, the pandemic has forced corporates to put that in action for application access to WFH and mobile users. This year significant acceleration in transformation has taken place around Digital Initiatives, including application modernization, cloud adoption, and Work from anywhere. A decade’s worth of transformation took place in a year, across how the business is conducted, and how we collaborate. This must mean that how we protect our network & Architect Security needs to also have a cutting-edge approach.
This transformation made more user work being performed off the enterprise network than on the enterprise network, more workloads running in IaaS than running in the enterprise data center, more applications consumed via SaaS than consumed from enterprise infrastructure, more user traffic destined for public cloud services than to the enterprise data center, more traffic from branch offices heading to public clouds than to the enterprise data center.
This cloud transformation has resulted in DC becoming a choke point and why would one design an architecture that makes traffic trombone between DC & cloud that means the availability of the cloud depends on the availability of DC.
The Journey to the Cloud
Before diving into the specifics of SASE, it’s important to understand a bit about this new term -SASE!
No doubt software-defined networking (SDN) paved the way for our realization of Zero Trust which in turn led to SASE with more security features bundled as a service. It is important to understand what business problems SDNs solve to get a clear idea of how to consume SASE.
Let me share an experience from one of our customers that helped transformed traditional networking for one of India’s largest media houses into an SDN backbone. While doing a presentation to their board, I had raised the following questions that were aimed at solving their current business problems,
- What if it (New SDN Solution) dramatically reduces application access time and significantly improves the end-user experience with added security?
- What if VC with MD & chairman never impacted? You would not need to worry about bandwidth & links going unstable.
- What if all the IT staff in Lutyens bungalow & remote branches were leveraged for other important tasks?
- What if you could leverage high-speed broadband links & 4G LTE in all remote locations for enterprise connectivity, and didn’t need to worry about unstable MPLS pipes?
- What if you can prioritize business applications over social networking traffic? And this kind of QoS policy was automatically applied by the respective router at branches and HQ?
- What if all this optimization were achieved without having to increase your bandwidth rather than WAN optimization creating room for additional traffic?
These questions obviously really excited them, but there were a lot of questions in return on how it would be achieved and how the new architecture would be like, that is when our VP Technology Srikant M pitched in.
It is quite a scene when Srikant gets out of his chair pulls his sleeves up and starts whiteboarding. Sometimes that itself wins the customer over! He explained in detail about how the new architecture would look like to the switch level and explained various data flows, he was just short of getting his hands on explaining the low-level architecture.
To support our theory, we also explained about a large and very complex mission-critical project we did for national security. They being in media knew all the headlines and were privy to what wasn’t making headlines too. The CIO asked ‘SHI India(Formerly Locuz) did that project? I nodded my head with pride.
Coming back to our discussion on SASE, what is SASE? SASE is the convergence of wide-area networking or WAN, and network security services like CASB, FWaaS, and Zero Trust, into a single, cloud-delivered service model.
This new normal of mobile and remote computing introduces new networking and security challenges that traditional remote access connectivity is not designed to address. Mobile computing poses several risks like phishing (mobile channels, such as text messaging, Facebook Messenger, WhatsApp, and phony websites that look legitimate), Mobile Malware (This risk of infection by malware on mobile devices is often higher than on desktop or laptop computers because most mobile users don’t install antimalware software on their smartphones and tablets and don’t recognize the threat), Fake public Wi-Fi networks, Malicious Apps from the Internet (including the Apple App Store and Google Play Store), Data Leaks. Branch network & remote access posed challenges like Routing complexity, Inefficient bandwidth usage, Loss of visibility & control, Lack of integrations & Interoperability, Management Complexity.
With this backdrop, if I have to go back to the same customer today with SASE and pitched it being technologically realistic, I would have tweaked some of my earlier questions to solve the cloud pain points,
- What if private application access is given without network access?
- What if we mask applications from the internet with outbound connections?
- What if we can go passwordless?
- What if we can go VPN less?
- What if you reduce the attack surface to the level where DDoS and Lateral Movement become the thing of the past?
- What if you see roaming user’s visibility beyond IP address and port number?
- What if it brings security and policy close to the user to eradicate unnecessary backhaul?
- What if Proxy-based architecture were used for a full inspection of encrypted traffic at scale?
- What if the Browser access service eliminates the need for a client on devices?
- What if the internet becomes the enterprise’s new transport network?
It is evident from the above that SASE solves the most critical challenges of modern-day, cloud-first IT challenges.
The SASE Vision
SASE addresses this shift in networking & security with a new architecture that converges networking and security services into one unified, cloud-delivered solution.
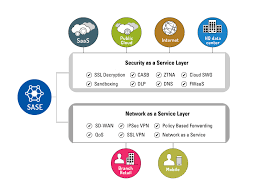
Tenets of an Effective SASE Solution
The COVID-19 pandemic has forever shifted the way businesses operate. Many applications are webified, HTTP is the new TCP. Removing multiple point products and adopting a single cloud-delivered SASE solution is the need of the hour. Following are some of the important features of any SASE solution you should look for when you are evaluating one.
Software-Defined Wide Area Network
An effective SASE solution must offer an integrated SD-WAN solution that should be application-defined rather than packet-based for better application visibility, enabling app SLAs that include SaaS, cloud, and unified communications as a service (UCaaS).
Zero Trust Network Access
A SASE solution should incorporate ZTNA for protecting applications as well as apply other security services for the consistent enforcement of data loss prevention (DLP) and threat prevention policies.
Read my detailed blog on Zero Trust Network Access (ZTNA) here.
Cloud Access Security Broker
Your SASE solution should incorporate both inline and API-based SaaS controls for governance, access controls, and data protection. To provide superior visibility, management, security, and zero-day protection against emerging threats, SASE should combine inline and API-based security as well as contextual controls. This is also called a multi-mode CASB.
SaaS visibility
- Discovery of shadow IT
- App discovery
- App usage reporting
- App risk assessment
- Configuration assessment
Control and Compliance
- App access control
- Data discovery and classification
- Compliance reporting and remediation
- Unmanaged device access control
SaaS Protection
- Threat protection
- Data protection
- Encryption
- Rights management
- User anomaly detection
- Workflow integration
Firewall as a Service
A SASE solution should enable FWaaS capabilities equivalent to the protection of a next-generation firewall by implementing a network security policy in the cloud. It should also have threat prevention services and DNS security.
FWaaS ideally should have the following features, Aggregate all traffic from multiple sources (for example, on-site data centers, branch offices, mobile users, cloud infrastructure) into the cloud.
Consistently apply and enforce security policies (fewer error-prone, manual configurations) across all locations and users.
Gain complete visibility into and control over their networks without having to deploy physical appliances, thereby reducing support costs.
Secure Web Gateway
A SASE solution should include the same security services as a traditional SWG, allowing organizations to control access to the web and enforce security policies that protect users from hostile websites or inappropriate content. Combined with DNS security and an explicit proxy, SWG provides a simple onboarding mechanism for organizations to transition to a SASE architecture.
A SASE solution moves SWG into the cloud, providing protection in the cloud through a unified platform for complete visibility and control over the entire network.
Digital Experience Monitoring
Autonomous digital experience monitoring (ADEM) provides end-to-end visibility and insights to create a seamless digital user experience. As the users are WFH, SASE solution should incorporate ADEM for comprehensive visibility, automated remediation, and detailed performance insights into endpoint devices, Wi-Fi, network paths, and applications.
Threat Prevention
- SASE solution should have Continuous and effective threat prevention, detection, and automated response across your environment, Granular visibility into your users, apps, and data.
- Advanced threat prevention over the network.
- Threat detection and analysis by correlating risky configurations, anomalous user and network activity, host vulnerabilities, and threat intelligence gathered from multiple data sources.
- Automated response to simplify security event triage.
- Cloud context to expedite security investigations.
Data Loss Prevention
With SASE, DLP should come as an embedded, cloud-delivered service to accurately and consistently identify, monitor, and protect sensitive data everywhere—across networks, clouds, and users.
DLP allows a company to, Discover all their sensitive data consistently across different repositories and communication vectors, such as Office 365, Box, Slack, corporate devices, network traffic, and so on. Monitor usage of sensitive data. Protect sensitive data and proactively prevent data leakage.
Internet of Things
The world is becoming smart with smart homes, smart cities, smartphones, smartwatches, etc. A SASE solution should have IoT security should be integrated into the platform to secure remote branches, sites, and workers from the cloud.
At SHI India (Formerly Locuz), we carry two-decade worth of experience in transforming networks, data centers to the cloud. We would love to be part of your digital transformation journey bringing invaluable experiences gained through decades of technology lead transformations.
Contact Us to find out more details and best practices on developing SASE adoption program, or for help getting started or moving to the next step.
Related Topics:
Application Security in a Cloud First World


