Application Security in a Cloud First World
History is replete with anecdotes of engineers building secure information systems and hackers attempting to obtain unauthorized access to those systems. If you have watched the movie called The Imitation Games, where Benedict Cumberbatch brilliantly portrays the legendary English mathematician, Alan Turing, you would know of one of the earliest known cases of “hacking” that changed the course of the history of mankind. Turing co-invented a machine known as Bombe that significantly reduced the work of code breakers in the Allied Forces to decipher signals that were sent by the German Air Force. Turing went on to develop a technique called Banburismus that decoded German Naval Codes and helped Allies win the Battle of the Atlantic.
Unfortunately, not all such attempts at gaining unauthorized access to a computer system have been as good-intentioned. There are plenty, of which there is scant knowledge in the public domain, and for good reasons.
In the past few years, there has been a conscious movement to the cloud and organizations have accelerated this movement because they realized measurable benefits from this transition. If one were to look closely, most of the cloud-based computer power and data storage that organizations consume stems from running their business applications. These applications could be any SaaS provisioned application that could be supporting one or several functions within the organization from Sales and Marketing to Logistics Execution and Manufacturing. Essentially, the enterprise operation has moved precious enterprise and personal data along with it to the cloud. This attracts cybercriminals as they see the possibility of getting access to vast troves of mission-critical and personal data and use them for nefarious purposes.
Securing an organization’s business applications has never been as important as it is today. But are solution providers and organizations giving it the importance it deserves? Established organizations often have a mature network and infrastructure security program that accounts for most of their IT security budget. As a relative newcomer, web application security tends to receive far less spending there. At the same time, web applications have become the main target for cybercriminals and now account for 75 percent of data breaches worldwide. Web application security has never been more important – and yet there is still some confusion as to its place in the overall security posture.
What is the state of application security? Why is it neglected?
Every organization has embarked on one or several digital transformation initiatives. Eventually, it all reduces to organizations using more cloud-native business applications in a variety of business areas. This has made collaboration easier and brought down departmental silos, especially by adopting an API-centric integration philosophy – an approach that enables business applications from various vendors to speak to each other through a universal communication protocol.
To keep up with the blindingly fast pace of application adoption, developers have had to rely on open-source components to compress their delivery schedules, often making serious compromises on the security aspect of those applications. These open-source components and frameworks have severe security vulnerabilities. Most of these originate from outdated third-party components that have been released under the open-source umbrella but have been poorly maintained, resulting in critical security gaps creeping in overtime.
What’s worse is that a network of applications, now connected via these vulnerable APIs, has produced an increasing attack surface, giving hackers more entry points to break into these business applications than ever before. But why has it come to this?
There is a noticeable ‘friction’ between application security & information or network security functions within an organization. We generally see the following trends
- Development and quality assurance (QA) are often standalone functions that are not well integrated with information security initiatives or business goals.
- The very people who are developing and testing the software are often not at the table when security features, threat modeling, and compliance requirements are being discussed.
Because of these unsaid gaps, application developers are not being given the opportunity to completely grasp the seriousness of vulnerabilities that they are baking into the product they deploy. By the time the “network security” team takes over this KPI, it is far too late, and organizations can only be reactive in such a situation. That’s half the battle lost because then security teams are planning risk mitigation strategies to deal with possible breach scenarios instead of pro-actively contributing to making the application architecture more robust.
What should be done?
There is no one size fits all solution and like with any other fundamental problem, organizations must approach improving application security as a product lifecycle problem. Moreover, there is no specific framework to “apply” security best practices to an application. Instead, development teams must look at incorporating security across the stack, starting from the web layer to the complete application ecosystem that includes dedicated attention to API security, database security, network, and end-point security to ensure overall application security.
This is important because modern web applications are built by combining several products and technologies. Developers typically start with their preferred choice of a web application framework that provides the design backbone and ensures that vital mundane tasks such as rendering the user interface or ensuring crow-browser support are taken care of. Developers then work within the framework to code the application logic, bringing in external libraries (often open-source) to provide specific features. Coupled with other external resources such as styles, fonts, and icons, the resulting web application is a complex network of dependencies. Each external component can have its own development history and its own vulnerabilities, making security testing a complicated task. As a result, developers and solution architects need to ensure security aspects on several dimensions including the following:
- Critical Infrastructure and Cybersecurity
- Mobile and Network Application Security
- Network Security
- Cloud Security
- Internet of Things Security
This means that coding to ensure security is no longer an option, but a necessity. Good security starts with a good design that considers the distributed nature of the application. DevSecOps evolves the DevOps philosophy to include security earlier in the development process. But what does this mean in terms of practice?
Putting it into practice – Adopting a DevSecOps Approach
The adoption of a DevSecOps approach is key for ensuring the security of your application throughout the entire secure development life cycle, as opposed to treating security as an add-on. This “shift-left” approach means every security incident should be resolved as quickly as possible. But before that, security – as a hard requirement in every application, must be baked into the product from as early a stage as possible, rather than it being an afterthought.
Another important aspect is the instrumentation of web applications from the security perspective. While developers build in advanced capabilities to capture every user input, from taps to monitoring the attention gaze, equal emphasis should be placed on incorporating security metrics and visibility criteria in all web and mobile applications. This will not merely help developers monitor security risks in real-time but give various security teams a clear and actionable dashboard to quantify and monitor security threats emerging from each application.
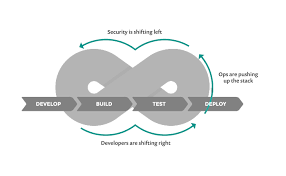
This requires Product Managers and Owners to include security KPIs in their product roadmaps and include several guidelines that allow adequate risk mitigation strategies to be adopted by organizations using these applications. Among them, the following are noteworthy:
- Enable app team to move quicker and security teams to prioritize efforts through shared, actionable real-time application security data.
- Support modern architecture that won’t break production and provide seamless strategic and tactical visibility.
- Provide reliable blocking with no required tuning and no performance degradation.
With the above framework in place, application teams will be better prepared to thwart any potential breach attempt and will be able to plan actively rather than be reactive in the event of an impending threat.
Roadmap for Application Security
We recommend organizations and developers alike institutionalize a few measures to ensure threat protection on business applications. We list a few for your reference below:
- Perform an application security maturity assessment: Maturity assessments bring forth existing gaps in the security apparatus, risk areas, and threat vectors. These are then provided in the context of the business impacts of risks, scalability, and a security road map to meet business objectives for a given period of time. Armed with this critical information organizations can set forth on their application security journey and define key priority areas.
- Secure Application Landscape: If your applications are hosted in a co-location or data center, make sure that your security strategy includes defense that covers the application layer with WAF, DDoS, Load Balancers, Content Filtering, Network Perimeter Layer security with advanced firewalls, and IPS. Also needed, is strong web security with the proxy that includes a strong underlying endpoint security management system. In order to monitor applications, Identity and Access Management (IAM), SSO & PAM solutions are invaluable that help in the detection of threats in such an event.
- It is also important to have an Application Performance Monitoring (APM) tool for real-time visibility into application services and get visibility of important KPIs. Modern data analytics platforms have the capability to index machine data in virtually any format that can give good insights into the application ecosystem. This is significantly better than that of an APM tool as APM tools are completely blind to network & virtualization layers. Security Analytics platforms can also help map services with KPIs in order to accurately pinpoint ‘where is the problem’.
- Adopt DevSecOps – Use Application Security Testing (AST) tools: Organizations must adopt DevSecOps application security tools that look for known vulnerabilities and classify results. They can be used to identify trends and patterns of attempted hacking attempts; breaches often exploit the application layer to access systems. Additionally, Application Security Tools (AST) are critical for improving application layer security. They help developers test for known vulnerabilities (or programming errors) during the build and release phases.
- Developers have the option of using one of several AST in their CI/CD process including Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and Interactive Application Security Testing (IAST). Aligning security testing with agile development, REST API Security, Mobile Application Security and Threat Modelling (Remote, Privacy) are other important ingredients of a robust application security program that must be incorporated in the application lifecycle.
- Don’t merely find vulnerabilities but mitigate or remediate them: Developers must focus on Penetration Testing. Even if code reviews with AST tools are standard practice, there is a possibility of residual vulnerabilities escaping to the production environment. Vulnerability scanning would unearth such loopholes, qualify them if they can be a threat and eventually become a risk. A Penetration Test verifies if these vulnerabilities can be exploited, and new age Penetration Test tools backed by human expertise can greatly help in finding security vulnerabilities in applications that lead to breaches and help in reducing the overall attack surface.
- Benefit from BaaS, FaaS by moving into the cloud: Utilising Baas such as Google Firebase or FaaS such as AWS Lambda solutions reduce the complexity of the backend infrastructure, making it easier for developers to build and release secure code in cloud environments. Such an approach reduces the potential attack surface and mitigates intrusion risks on the application level.
- Adopt the philosophy of Zero Trust Network Access: Organization must move private applications to the cloud and adopt a Zero Trust Network Access approach that helps in eliminating traditional VPNs and passwords, facilitates micro-segmentation of applications, provides application access without network access, masks applications from the internet with outbound connections and provides overall a higher level of security.
Read my detailed blog on ZTNA here https://www.locuz.com/blog-details/Future-of-Networking-ZTNA
- Take application security to the masses: Organizations must invest in training developers on Application Security measures and build security metrics in their KPIs. This is a proven way to incentivize focus on application security and yields excellent long-term results for organizations and developers alike.
- Measure and iterate: Organizations must continually monitor security metrics and iterate their approach to securing the business application layer. This can only be done with robust product instrumentation and a healthy review policy that is driven by the leadership.
- Make a continuous inventory of your development components: Organizations must create an inventory of all components and the versions used in development. This provides an easy way to update a component to the latest version if a vulnerability is discovered or published publicly.
While adopting these approaches there is no guarantee that an application will not be compromised. However, adherence to these guidelines can significantly reduce the probability of such an eventuality.
At SHI India (Formerly Locuz), we have helped several companies, large and small, through their journey of securing their application security maturity process. Contact us to find out more about our process and how we can work together to create better outcomes for your company.
Related Topics:
Secure Access Service Edge (SASE) – All you need to know!
Cloud Native and App Modernization Security concerns – Exploring Container Security


